This is the fourth article in my seven-part series on the Google Cloud Architecture Framework.
Article 1: Google Cloud Architecture Framework: Overview
Article 2: Google Cloud Architecture Framework : System design
Article 3: Google Cloud Architecture Framework : Operational Excellence
Security is vital in cloud computing to protect data, ensure compliance, maintain trust, and mitigate risks, ultimately enabling organizations to leverage the benefits of cloud technology securely and responsibly. Apart from Data Security which is the first thing that comes to our mind when we think about Cloud, there are other aspects which are equally important like Network Security, Compliance and Governance, Infrastructure Security & Application Security.
Security, Privacy and Compliance category in the Google Cloud Architecture Framework shows you how to architect and operate secure services on Google Cloud. The Architecture Framework defines some of the available products and services, offers implementation recommendations, and outlines best practices. When migrating workloads to Google Cloud, you must assess your business needs, risks, security measures, and compliance requirements. This document assists you in creating a safe Google Cloud solution.
Google core principles include defense in depth, at scale, and by default. In Google Cloud, data and systems are protected through multiple layered defenses using policies and controls that are configured across IAM, encryption, networking, detection, logging, and monitoring.
Shared responsibility and Shared fate
It’s critical to comprehend the shared responsibility model in order to choose the appropriate Google Cloud data and workload protection strategy. The shared responsibility model outlines your responsibilities for cloud security as well as how these responsibilities differ for cloud providers.
GCP’s creation and management of a reliable cloud infrastructure for client workloads is part of the shared fate. To help customers deploy their workloads securely, GCP offers certified infrastructure code and best practice guidelines. GCP release solutions that combine various Google Cloud services to solve complex security problems and we offer innovative insurance options to help users measure and mitigate the risks that they must accept.
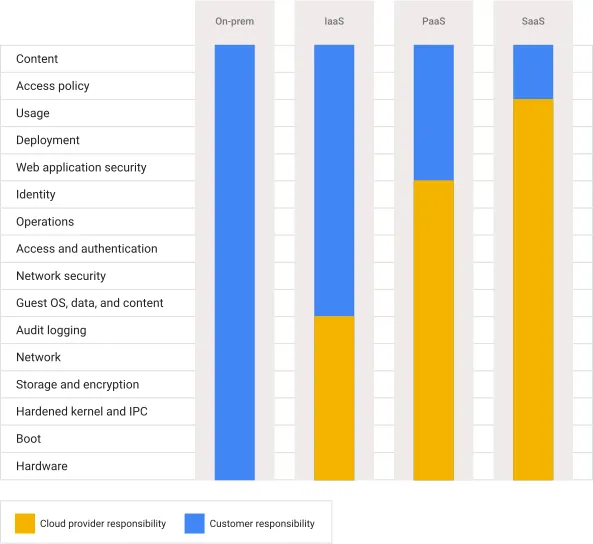
This image shows briefly, what responsibilities are taken care by GCP and Customers in different types of architectures
Security Principles
This document explains core principles for running secure and compliant services on Google Cloud. Many of the security principles that you’re familiar with in your on-premises environment apply to cloud environments.
These are some guidelines and best practices for helping you build and run a Secured cloud architecture:
1. Use a defense-in-depth strategy to implement security in your application and infrastructure at every level.
2. When possible, simplify system architecture to allow for flexibility, and make sure that each component’s security requirements are documented.
3. Automate deployment of sensitive tasks.
4. To monitor your infrastructure and application, use automated tools. Use automated scanning in your CI/CD pipelines to find security incidents and check your infrastructure for vulnerabilities.
5. Meet the compliance requirements for your regions. Where possible, automate your compliance efforts with the help of Sensitive Data Protection and Dataflow to automate the PII redaction job.
6. Comply with data residency and sovereignty requirements. To help comply with data residency requirements, Google Cloud lets you control where data is stored, how data is accessed, and how it’s processed.
Manage risk with controls
This document describes best practices for managing risks in a cloud deployment. Performing a careful analysis of the risks that apply to your organization allows you to determine the security controls that you require. You should complete risk analysis before you deploy workloads on Google Cloud, and regularly afterwards as your business needs, regulatory requirements, and the threats relevant to your organization change.
There are two aspects of Risk management:
- Identify risks to your organization:
Conduct a risk assessment to identify the security elements you require to meet your internal security requirements and external regulatory requirements before creating and deploying resources on Google Cloud. Your risk assessment gives you a list of hazards that are specific to you and indicates the degree to which your company can identify and mitigate security threats. Your shared responsibility agreement with your cloud provider makes your risks in a cloud environment different from your risks in an on-premises environment.
GCP provides multiple services which can be used for risk assessment. Like Cloud Security Alliance, models such as OWASP application threat modeling that provide you with a list of potential gaps, Risk Manager To help catalog the risks.
2. Mitigate your risks:
Technical controls, contractual protections, and third-party verifications or attestations can all be used to reduce risk. You can utilize these mitigations when you implement new public cloud services.
Technical controls like these are very useful:
I) Use of Cloud VPN and Cloud Interconnect.
II) Audit logs and monitoring
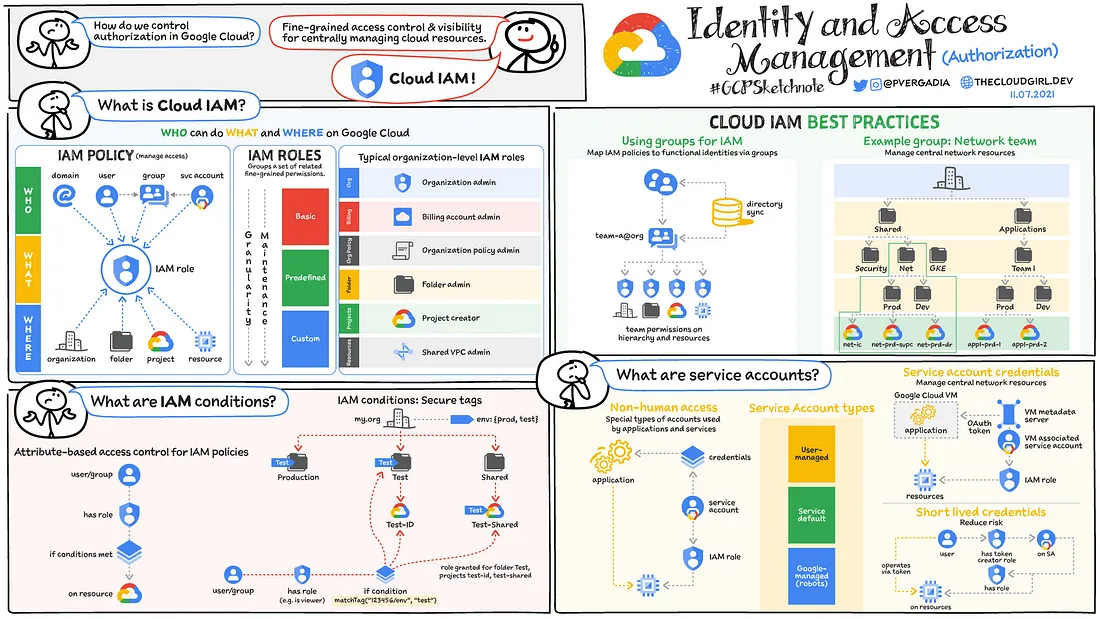
Manage identity and access
This document provides best practices for managing identity and access. The practice of IAM helps you ensure that the right people can access the right resources by addressing important aspects of authentication and authorization.
These are some guidelines and best practices for helping you implement best IAM for you cloud deployments:
1. Use a single identity provider. It can be Active Directory, Cloud Identity Premium or Google Workspace to manage identities for users.
2. Protect the super admin account by Creating a new account for this purpose; don’t use an existing user account.
3. Plan your use of service accounts. When you use service accounts, you must consider an appropriate segregation of duties during your design process.
4. Update your identity processes for the cloud. This helps in future with audit logs which can show Administrator activity as well as Data access activity.
5. Set up SSO and MFA. This is a must !
6. Implement least privilege and separation of duties. With users as well as Service Accounts.
7. To monitor the activities of privileged accounts for deviations from approved conditions, use Cloud Audit Logs.
8. Set restrictions on resources. This can be done with the help of Tags, IAM conditions or VPC Service Controls.
This is a very useful article to understand IAM with Google Cloud.
Implement compute and container security
Google Cloud includes controls to protect your compute resources and Google Kubernetes Engine (GKE) container resources. This document describes key controls and best practices for using them.
These are some guidelines and best practices for helping you implement compute and container security:
1. Use Shielded VM images when you require boot security, preventing malicious code from being loaded during the boot cycle, to deploy sensitive workloads.
2. Use Confidential Computing for processing sensitive data. Confidential data includes personally identifiable information (PII), financial data, and healthcare information.
3. Protect VMs and containers with the help of IAM.
4. Disable external IP addresses unless they’re necessary.
5. Keep your images and clusters up to date with path management.
6. Control access to your images and clusters with the use of services like IAM, VPC Service Controls etc.
Secure your network
The security ramifications of expanding your current network to include cloud environments are numerous. It’s likely that your on-premises multi-layered defensive strategy includes a separate barrier between your internal network and the internet. Most often, physical firewalls, routers, intrusion detection systems, and other devices are used to guard the perimeter. The boundary is well defined, so it’s easy to keep an eye out for intruders and take appropriate action.
You leave the on-premises boundary when you migrate to the cloud (fully or through a hybrid strategy). This document explains how to keep the workloads and data on Google Cloud safe for your company. Your business requirements and risk tolerance will determine how you configure and secure your Google Cloud network.
These are some guidelines and best practices for helping you implement network security:
1. Deploy zero trust networks. When verifying access requests, the zero trust security model requires you to check both the user’s identity and context.
2. Secure connections to your on-premises or multi-cloud environments. This can be achieved with the help of key services like Dedicated Interconnect, Partner Interconnect, Cross-Cloud Interconnect and VPN’s.
3. Disable default networks. It’s usually a best practice to limit these networks to one per project in order to enforce access control effectively.
4. Secure your perimeter using firewalls and VPC Service Controls.
5. Inspect your network traffic using different services like Cloud IDS, Packet Mirroring or any third-party tools to collect and inspect network traffic at scale. Inspecting network traffic in this way helps provide intrusion detection and application performance monitoring.
6. Use a web application firewall to provide distributed denial-of-service (DDoS) protection and web application firewall (WAF) capabilities.
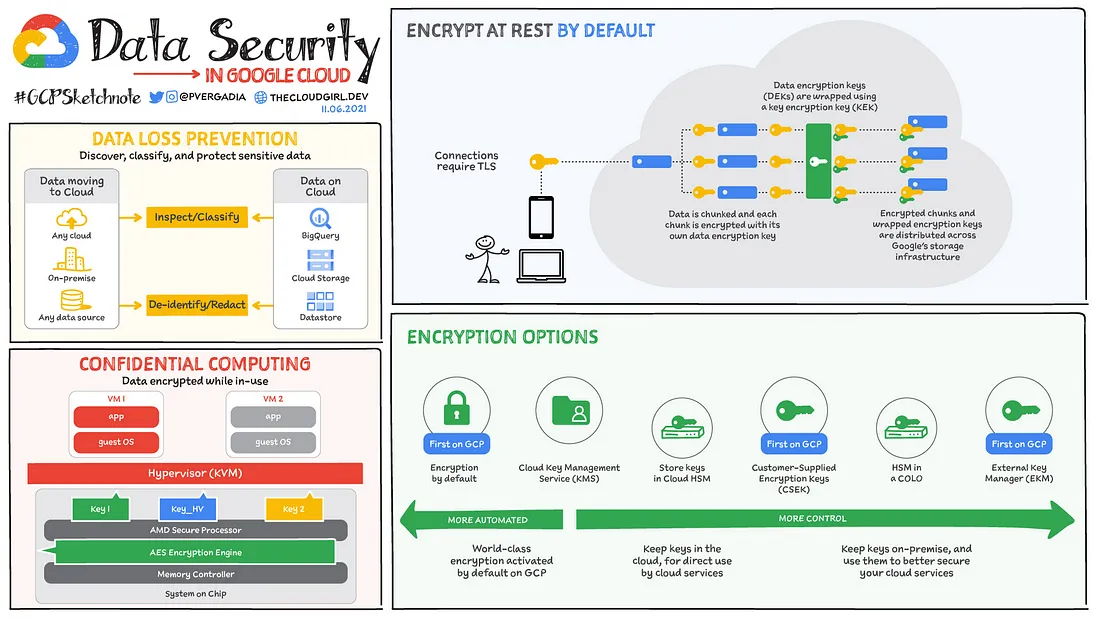
Implement data security
Data security is probably the most interesting and widely discussed topic whenever we talk about Cloud Security.
You must take into account the sensitivity of the data and what you intend to process and keep on Google Cloud when designing your deployment architecture. Create controls that will assist safeguard data throughout its lifecycle, identify data ownership and classification, and guard against unauthorized usage.
These are some guidelines and best practices for helping you implement Data security:
1. Automatically classify your data into categories like Public, Internal, Confidential & Restricted as early in the data management lifecycle as possible. We can use Sensitive Data Protection to discover and classify data across your Google Cloud environment.
2. Manage data governance using metadata to ensure that data is secure, private, accurate, available, and usable. Use Data Catalog for metadata management.
3. Protect data according to its lifecycle phase and classification. It can be done with the use of Identification (Using Cloud Identity and IAM), Boundary and access (Firewalls, VPC Service Controls).
4. Encrypt your data. By default GCP will Encrypt your data at the rest. To protect further one can use Customer-managed encryption keys, Customer-supplied encryption keys or Third-party key management system. This is one of the most important aspects of Data Security.
5. Control cloud administrators access to your data.
6. Configure where your data is stored and where users can access it from. You can control the network locations from which users can access data by using VPC Service Controls.
7. Manage secrets using Secret Manager.
8. Continuous Monitoring the data and Auditing the logs is very important and useful.
This is a very useful article to understand Data Security.
Manage compliance obligations
The cloud regulatory requirements depend on a combination of factors, including the following:
The laws and regulations that apply your organization’s physical locations.
The laws and regulations that apply to your customers’ physical locations.
Your industry’s regulatory requirements.
Three steps are usually involved in a compliance journey: assessment, gap remedy, and ongoing monitoring. The best practices for each step are covered in this section.
- Assess your compliance needs:
The first step in assessing compliance is to carefully examine all of your legal responsibilities and the ways in which your company is carrying them out. Use the Compliance resource center to assist you in evaluating Google Cloud services. - Deploy Assured Workloads:
Assured Workloads is the Google Cloud tool that builds on the controls within Google Cloud to help you meet your compliance obligations. - Review blueprints for templates and best practices that apply to your compliance regime:
Google has published blueprints and solutions guides that describe best practices and that provide Terraform modules to let you roll out an environment that helps you achieve compliance.
It covers important Standards followed around the world like PCI, FedRAMP & HIPAA. - Monitor your compliance:
There are a lot of services available with GCP which can help you with monitoring for compliances. Like Access Transparency, Firewall Rules Logging, VPC Flow Logs, Security Command Center Premium & Key Access Justifications.
Implement data residency and sovereignty requirements
Data residency and sovereignty requirements are based on your regional and industry-specific regulations, and different organizations might have different data sovereignty requirements.
1. Manage your data sovereignty. Data sovereignty provides you with a mechanism to prevent Google from accessing your data. This can be done using access controls and Storing and managing encryption keys outside the cloud.
2. Manage your operational sovereignty. Operational sovereignty provides you with assurances that Google personnel can’t compromise your workloads. This can be done by restricting the deployment and limiting Google personnel access on predefined attributes such as their citizenship or geographic location.
3. Manage software sovereignty. Software sovereignty gives you the guarantee that you won’t be dependent on or restricted to a single cloud provider, allowing you to manage the availability of your workloads and host them anywhere you choose. The ability to endure situations that force you to swiftly alter the locations of your workloads and the permissible levels of external connectivity is a key component of software sovereignty.
4. Control data residency. To help comply with data residency requirements, Google Cloud lets you control where your data is stored, how it is accessed, and how it’s processed.
Thank you for reading this article. Your time is appreciated.
Until next time, stay curious !!
For cloud computing infrastructures to be successful and reliable, security is essential. Organizations may reap the benefits of cloud technology while skillfully managing risks and guaranteeing the protection of sensitive data and resources by giving security first priority and putting strong security measures in place.
This was the fourth article in my seven-part series on the Google Cloud Architecture Framework. We will go into more detail about the remaining 3 pillars in my upcoming articles, along with an understanding of some best practices for creating and managing a well-architected framework on GCP.
